Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Descrição
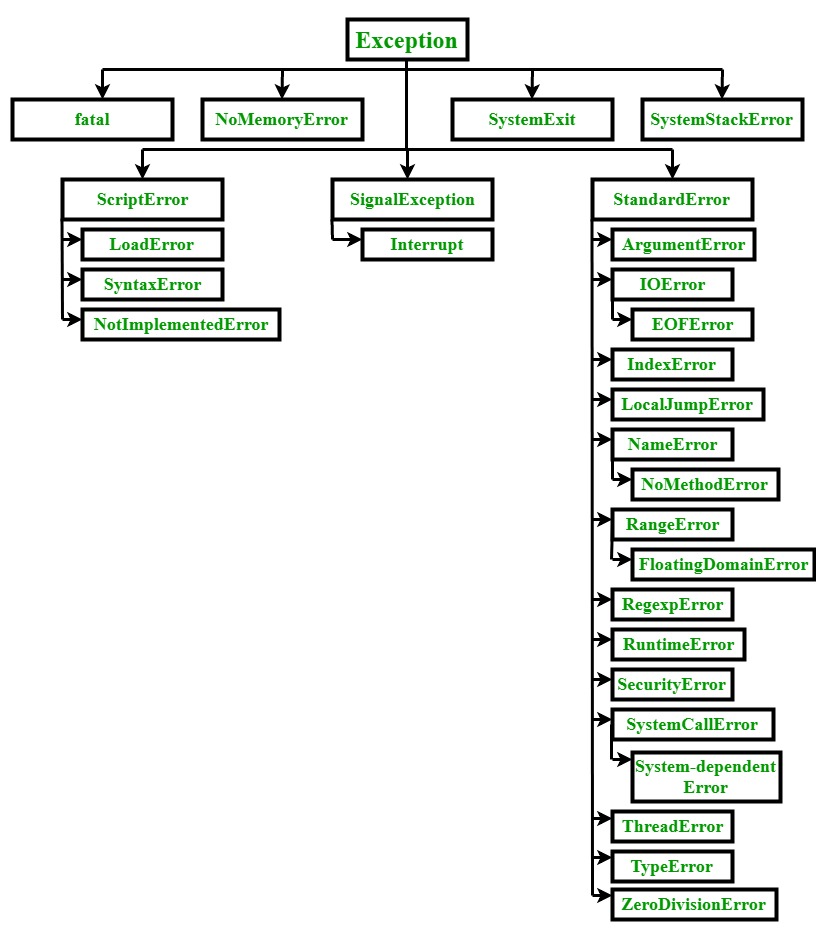
In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.

GitHub Actions Security Best Practices [cheat sheet included]

API security, vulnerabilities and common attacks

6379 - Pentesting Redis - HackTricks
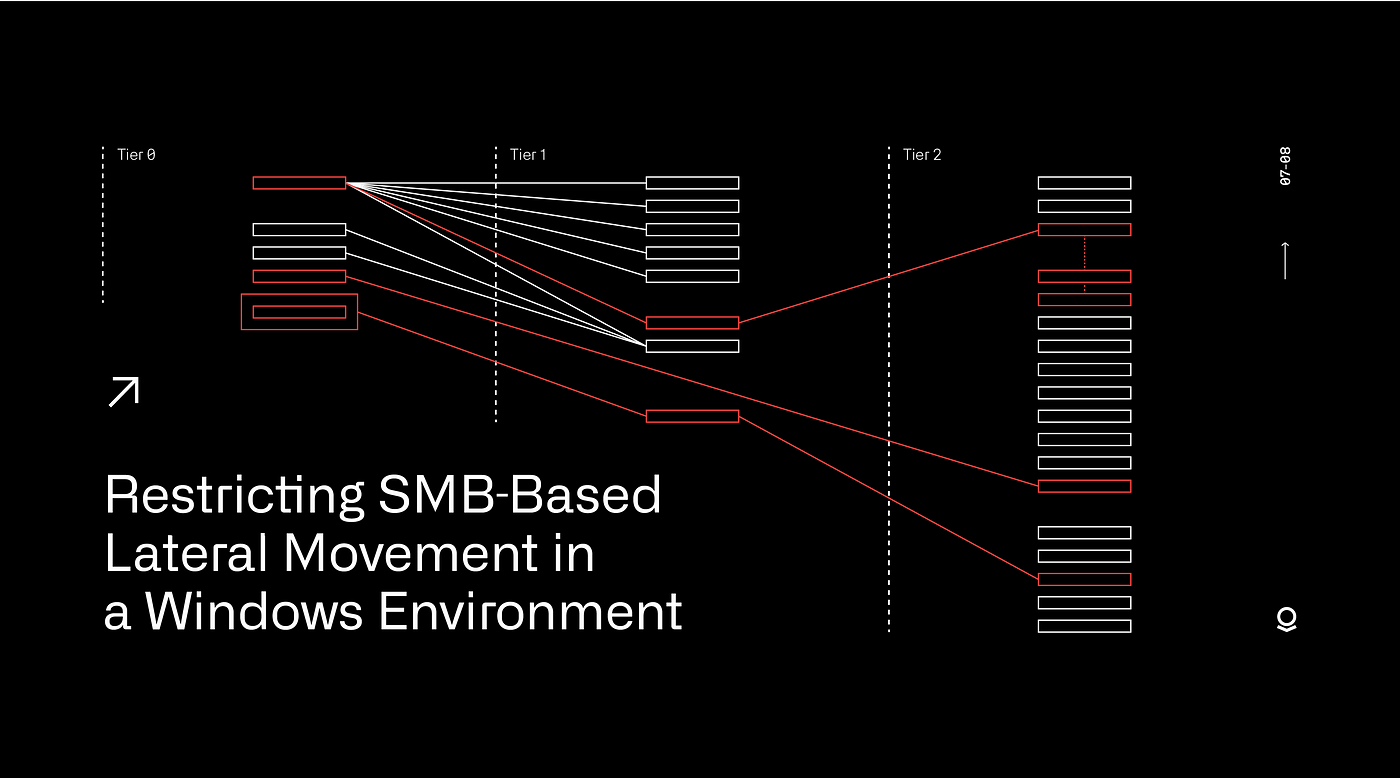
Restricting SMB-based Lateral Movement in a Windows Environment

Abusing Exceptions for Code Execution, Part 2

Hunting for Suspicious Windows Libraries for Execution and Defense
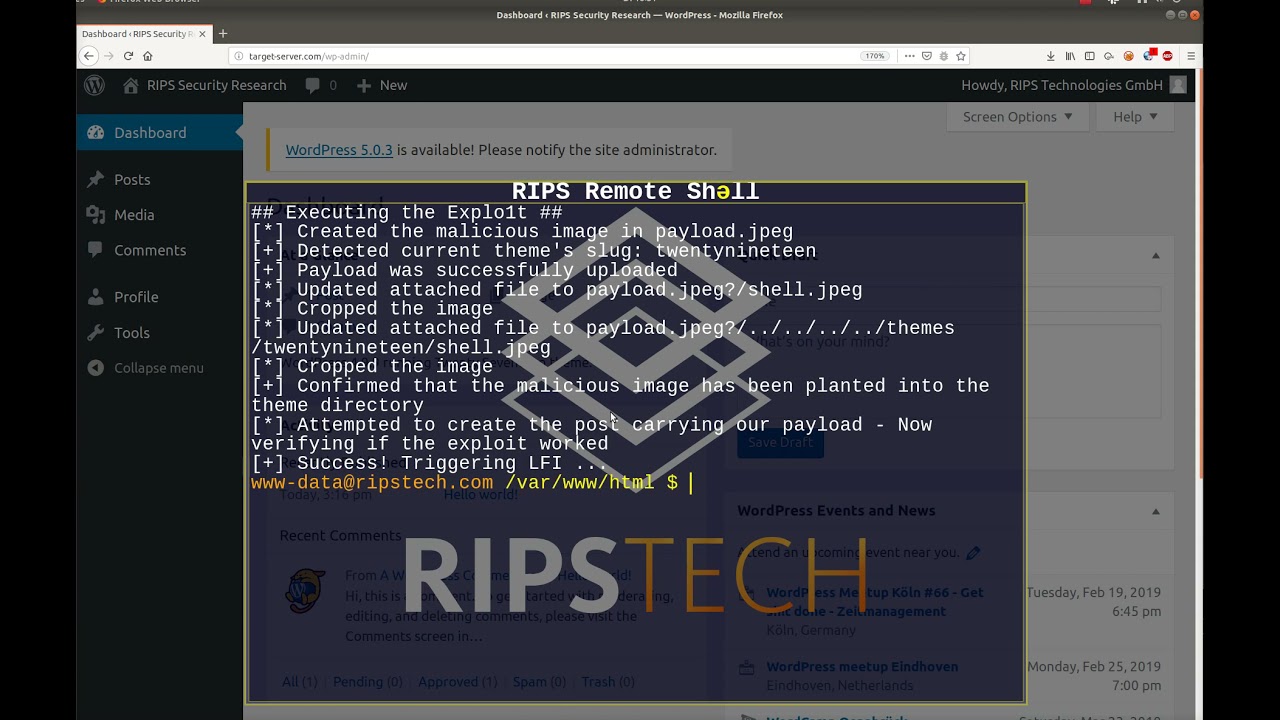
WordPress 5.0.0 Remote Code Execution

What is code injection?, Tutorial & examples
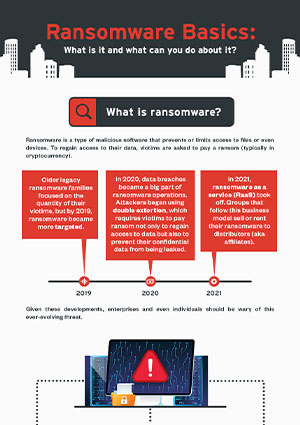
Ransomware - Definition

JavaScript sandbox vm2 remediates remote code execution risk
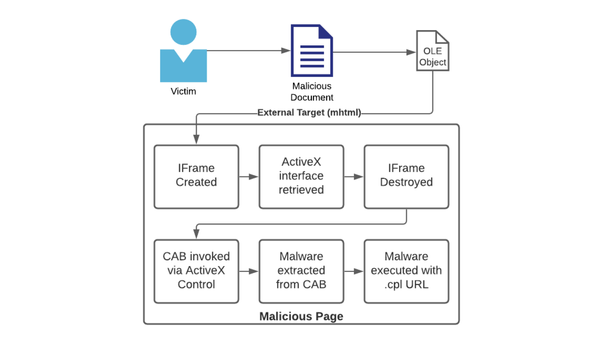
Abusing Exceptions for Code Execution, Part 2

General Tools Digital Angle Finder Ruler #822 - 5 Stainless Steel

Chiseling In: Lorenz Ransomware Group Cracks MiVoice And Calls
de
por adulto (o preço varia de acordo com o tamanho do grupo)